Sign up for a Free Trial scan
-
Locate all your (web)servers, either on premise or in the cloud
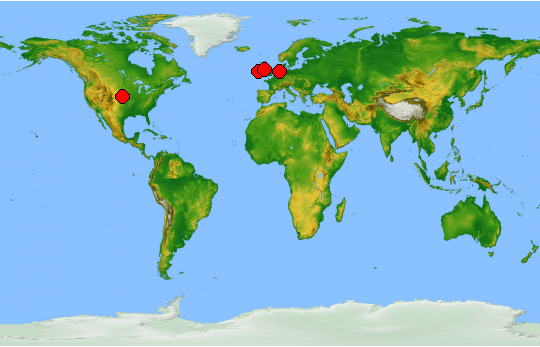
Get a list of the servers of the organization that are visible from the internet, based on public information. These are found by using google searches, links on the website, portscans around identified websites, and other public sources. This leads to an overview of websites that belong to the same organization, including their network location. Not only the well-known websites, but also test-servers, cloud-services and ‘forgotten’ marketing-servers.
-
Learn where the weak spots are
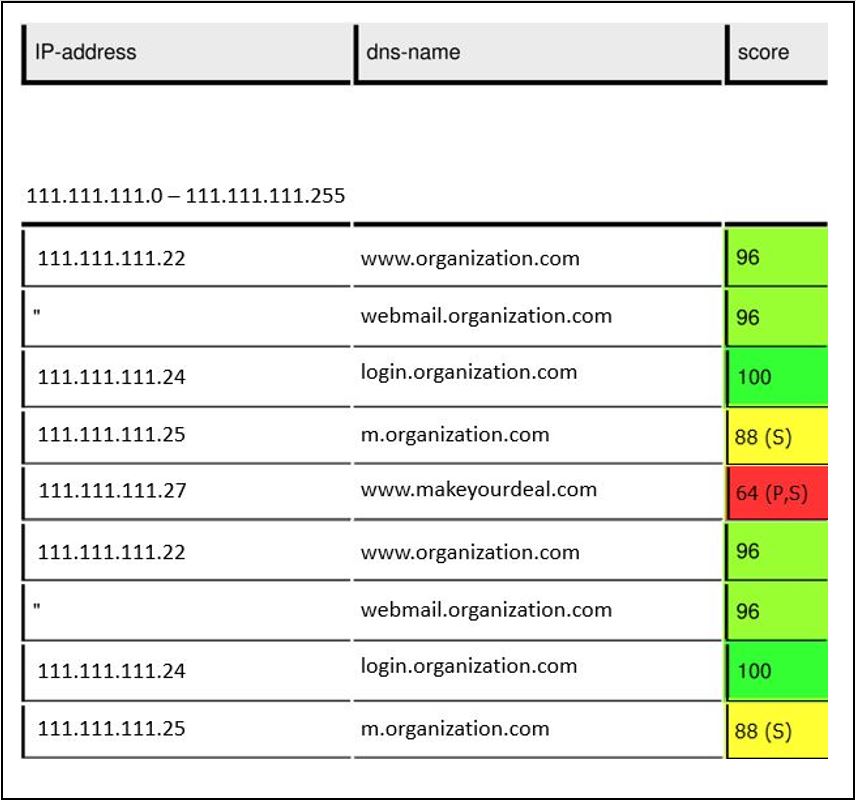
The servers are grouped by hosting location. It's immediately clear which servers are in the cloud, which are in house and which are hosted at a supplier. In addition to the domain inventory, security checks are done for a set of common vulnerabilities. The results help to focus on the most vulnerable servers, as well as on the associated management processes. The traffic-light colouring puts focus on the most vulnerable groups that need attention. The reports are in pdf-format and sent by e-mail.
-
Benchmark against peers

The monthly security score enables you to benchmark against other organizations. Your sector is scanned as well, and the security status of the whole sector is included in the report.
-
Keep an eye on mobile apps
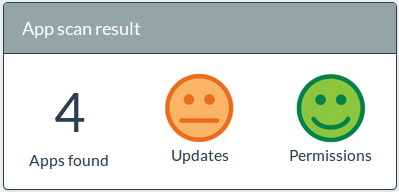
View a list of mobile apps that are developed or used by your organization.
Excessive security and privacy-related permissions are reported, as well as the last time they have been updated.
-
Monitor your e-mail reputation
Retrieve an overview of all mailservers in the domain, including those of your important suppliers and business partners. Deliverability and anti-phishing measures are checked. Act before business processes are disrupted, and before your clients start to block your e-mail.



